The crypto industry is facing a new wave of smart contract exploits.
According to recent reports from CertiK and De.Fi, over $3 billion was lost to protocol vulnerabilities in 2025 alone.
These attacks often target users who trust unaudited contracts — and most victims have no technical background at all.
The good news?
You don’t need to be a blockchain developer to spot basic red flags.
Here’s how to stay safe with simple, practical checks.
Why Smart Contract Attacks Are Rising
Smart contracts power everything from DeFi protocols to NFT marketplaces, but they’re also targets.
The main reasons behind the surge include:
- Rapid project launches without independent audits.
- Copy-pasted open-source code with hidden bugs.
- Poor liquidity locking and admin privileges that allow rug pulls.
Attackers exploit speed and hype — not necessarily complex coding flaws.
How to Check if a Contract Is Risky (No Coding Needed)
Even without programming skills, you can perform a few key safety checks:
1. Use Contract Scanners
Platforms like RugCheck, TokenSniffer, and GoPlus Security analyze contracts instantly.
They flag high-risk functions such as mint(), owner(), or unrestricted token transfers.
2. Verify the Source Code
Go to Etherscan or BscScan and make sure the contract is verified.
If you see “Source Code Not Verified”, that’s an immediate red flag.
3. Check Community and Audit Reports
Look for mentions on Twitter, Reddit, or project Discords.
A legit project will usually share its audit report (CertiK, Hacken, PeckShield).
If no audit is available, treat it as unaudited — regardless of promises.
Best Practices to Protect Your Wallet
- Avoid connecting your main wallet to new or unverified dApps.
- Use a burner wallet for testing unknown tokens or platforms.
- Revoke token approvals regularly via Revoke.cash.
- Stay skeptical of offers promising “instant rewards” or “1000% APY”.
Real Example: How a Simple Check Could Have Prevented a $10M Loss
In February 2025, an exploit on a DeFi yield platform drained $10 million within hours.
Auditors later revealed that a public owner() function allowed anyone to alter withdrawal limits.
A simple scan on RugCheck would have flagged the risk instantly.
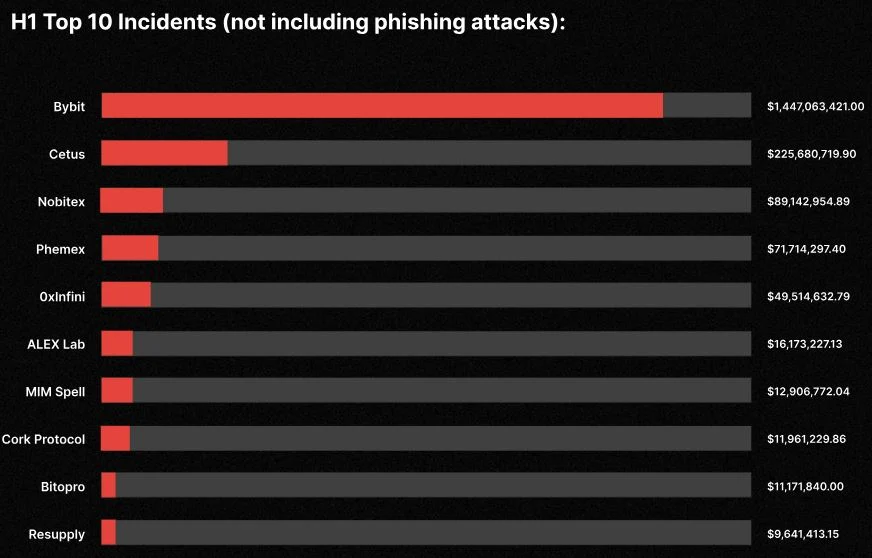
Source: Certik
Final Thoughts
Smart contract attacks aren’t slowing down — they’re evolving.
But awareness and a few easy tools can reduce your risk dramatically.
You don’t need deep technical expertise — just a habit of checking before trusting.
Stay curious. Stay cautious. And always verify before you connect.










